Sustaining Anonymity of Critical Nodes in Ad-hoc and Sensor Networks
| In many applications of ad-hoc and wireless sensor networks the bulk of the traffic is targeted to few nodes. For example, in a tactical edge network the gathered intelligence data about enemy troops flows towards field commanders and/or an in-situ base-station (BS). Another example is a wireless sensor network in which the BS collects data from a large number of sensor nodes that are distributed over a wide geographic area. Such a network operation pattern makes the BS a critical asset for these applications yet leaves it vulnerable. An adversary could cripple the network by simply disrupting or physically damaging the BS, without targeting individual data collectors (i.e., source nodes). The failure of the BS could also cause loss of important data that may not have been processed and could cause a major negative impact if the BS represents a commanding authority for the network. | ||
|
||
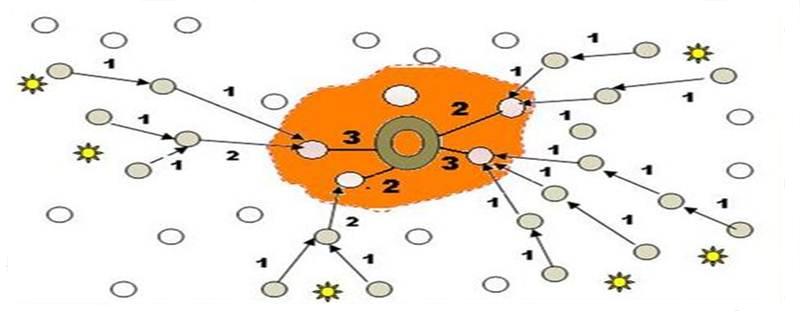
Furthermore, replacing a damaged BS may be infeasible given the remote and often inhospitable network environment (e.g., in a combat zone where BS access is extremely risky). In addition, providing a replacement BS will not avert the impending threat since the adversary could continue to damage the newly replaced BS once it is identified. Therefore, concealing the location of BS is of utmost importance for maintaining a robust network operation in a hostile environment. From an adversary's point of view, the problem of finding the BS’s location is made easier by the inherent traffic pattern in the network. The primary flow of traffic is from all nodes towards the BS over a relatively fixed multi-hop path. As data packets are transferred from sources towards the BS their paths merge when they approach the BS as shown in the Figure above. Hence, the nodes close to the BS must transmit comparatively more packets than nodes further away from the BS. The presence of increased traffic in the vicinity of the BS becomes noticeable to an eavesdropper. By observing this transmission sequence an adversary can begin to zoom in closer to the BS. Conventional network security methods such as packet encryption would not be effective in countering such a threat since an adversary could intercept the individual wireless transmission and employ traffic analysis techniques to follow the data paths. Since all active routes end at the BS, the adversary may be able to determine its location and launch targeted attacks. Employing spread spectrum or other physical-layer transmission security methods would not be a sufficient countermeasure for increasing BS anonymity as adversaries are becoming more advanced and equipped with sophisticated demodulation and decoding technologies. In addition, signal spreading reduces rather than eliminates the prospect of transmission detection. To counter such a threat, some techniques need to be employed in order to boost the anonymity of the BS. Anonymity in this context can be defined as concealing the identity, role and location of the BS from external observers. Contemporary anonymity models found in the literature do not consider the unique characteristics of the type of ad hoc and wireless sensor network networks described above. Our research opts to tackle such a challenging BS anonymity problem and develop a suite of techniques for countering the adversary’s attack and protecting the BS. We are currently investigating metrics for assessing the BS anonymity and developing techniques for countering traffic analysis and concealing the location, identity, and role of the BS. The scope of the investigation spans the physical, link, network and application layers of the target network’s communication protocol stack. We are also exploring the various architectural and threat models. A subset of recent work on the topic of BS anonymity is provided as a reference for the interested reader. |
||
| Recent Publication | ||
|
||